
Secure your site from 99% of online attacks…
Whether you’re a beginner or a seasoned developer, Guard Dog ensures your WordPress site remains protected around the clock.
Secure Your Site Today/ Supreme Security
All day every day your site is {secure}
SAFE & EASY
Guard Dog Security Service
This service provides a complete security solution to ensure your WordPress website is fully protected from threats and vulnerabilities. It safeguards critical files from unauthorized changes, blocks common hacker entry points, and restricts unauthorized access by securing your login page and user registration processes. We will also react to any infections your site might receive at no additional cost.
$47/per year for one site
Stay Secure
with full site security
Security at the highest level
Guard Dog gives you the highest level of security on your WordPress website
Site Lock (only here)
The “Site Lock” feature provides robust security for a WordPress website by restricting file writing on the server, which serves as a protective barrier against various forms of cyberattacks.
Move the Login Page
WordPress login security plays a critical role in safeguarding your website because it represents the first line of defense against unauthorized access. The login page is a primary target for attackers who may attempt to gain entry using various techniques.
User Registration Lock
An additional security feature is the ability to lock new user registration, which prevents unauthorized users from creating accounts. By enabling “Registration Locked,” you stop all new user registrations, ensuring that only the website administrator has control.
Security Headers
Security headers are essential HTTP response headers that strengthen your WordPress site’s defenses by mitigating various web-based attacks and reducing exposure to potential vulnerabilities.
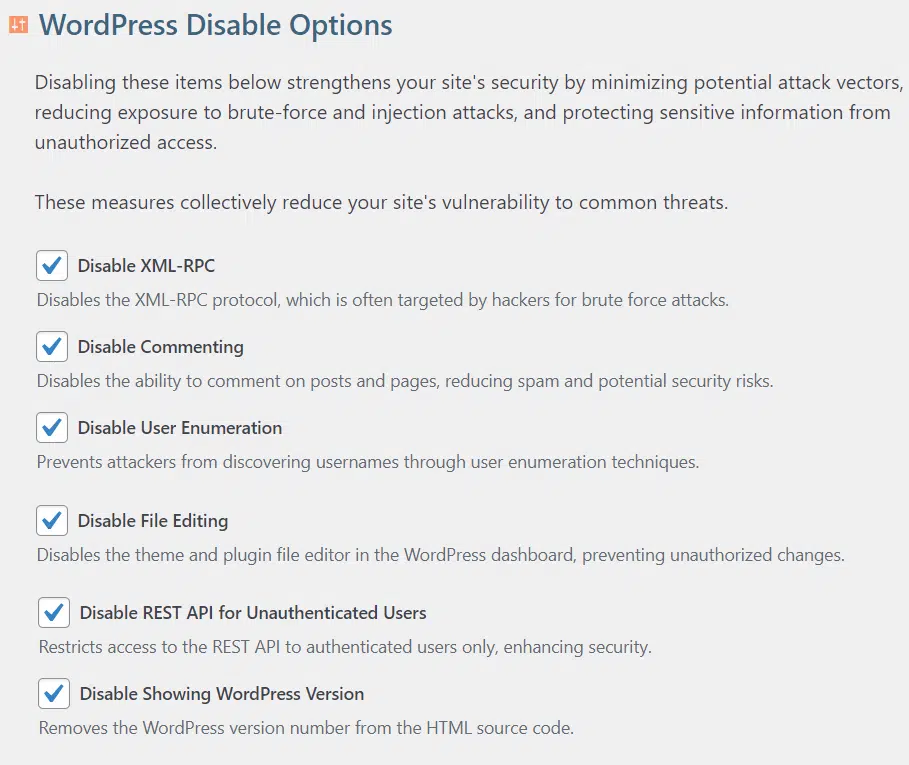
Disable Entry Points
Disabling specific WordPress features is a crucial step in fortifying your website against potential security risks. By turning off these items, you minimize the number of potential attack vectors and code injection vulnerabilities.
Security Reporting
The PDF security report generated by our Guard Dog Security plugin will provide a comprehensive overview of the site’s current security status, offering valuable insights into both secured aspects and areas requiring further attention.
Automated Reports
You have the ability to designate a single email address or multiple addresses to send out a full security report at a frequency of your choice which can be weekly, monthly or quarterly.
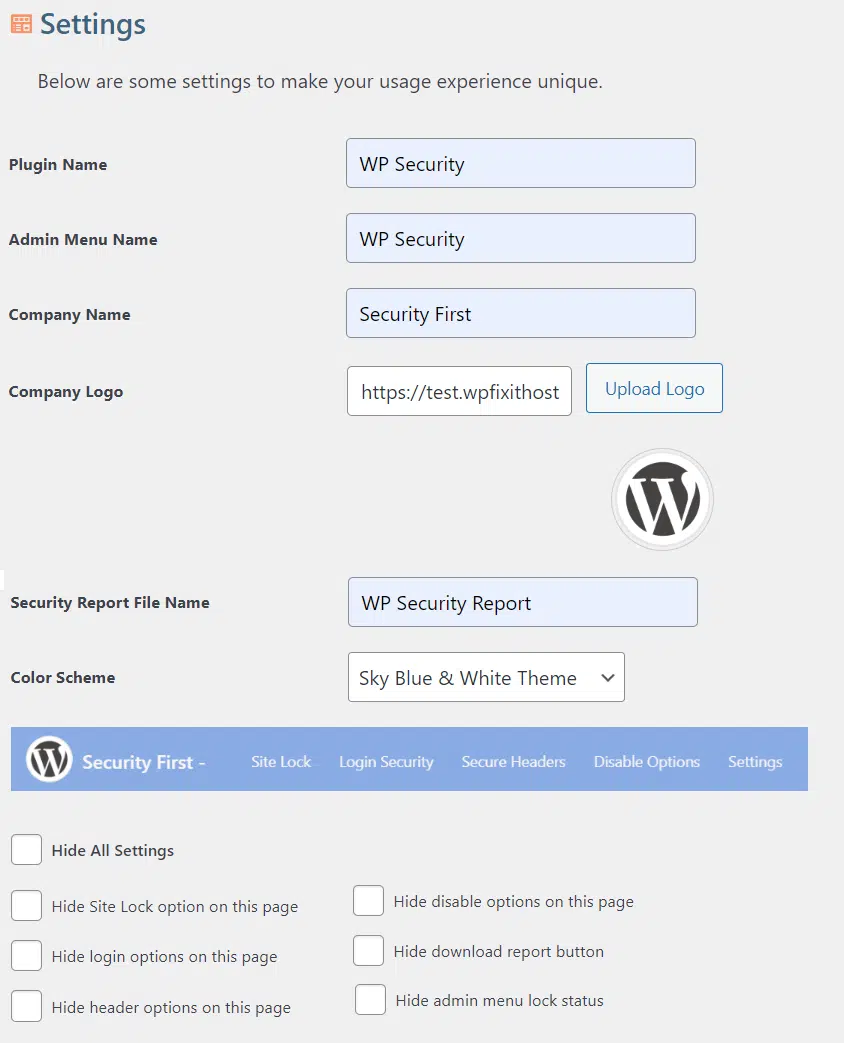
Customize Branding
The white label settings allow users to customize various aspects of the Guard Dog Security plugin, creating a unique and branded experience tailored to your organization.
Uncompromising WordPress Security

Have Impenetrable WordPress Protection
Having “Impenetrable WordPress Protection” means implementing robust and comprehensive measures to safeguard your WordPress website against various security threats.
Site Lock Security Feature
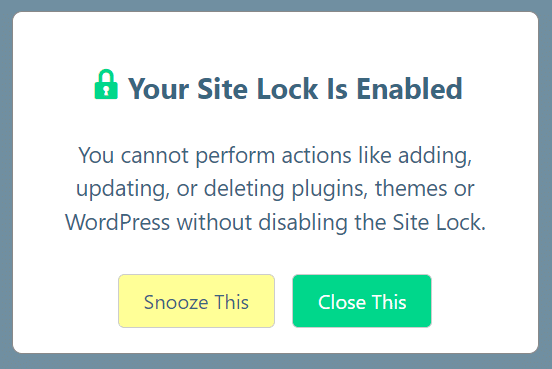
This feature restricts the ability to write, modify, or upload files on the server. It targets the critical WordPress folders that are common entry points for malicious activity.
Hackers can’t inject or upload files without write permissions, which drastically reduces the risk of unauthorized changes.
Prevents the introduction of malware, such as scripts or back doors, by blocking any file modifications.
Maintains the integrity of your files, ensuring that no malicious code is added or existing files are tampered with.
Reduces the chances of known and unknown vulnerabilities being exploited through file changes.
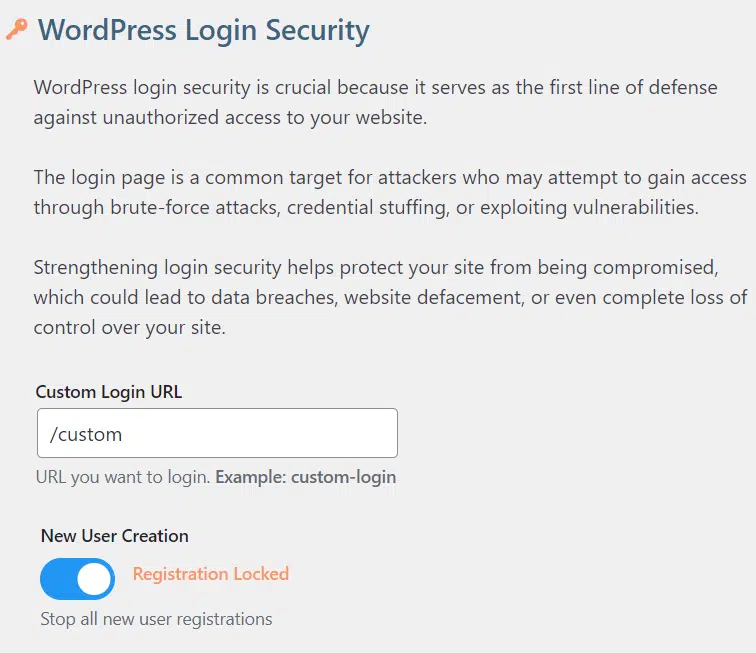
Login Control That is Easy
The WordPress login security plays a critical role in safeguarding your website because it represents the first line of defense against unauthorized access. The login page is a primary target for attackers who may attempt to gain entry.
One effective way to enhance login security is by setting a Custom Login URL. For example, changing the default login page URL (/wp-custom or /wp-login.php) to something unique like /eat or /custom-login makes it harder for attackers to locate the login page.
The ability to lock new user registration, which prevents unauthorized users from creating accounts. By enabling “Registration Locked,” you stop all new user registrations, ensuring that only the website administrator has control over who can access the site.

Lock Down Site Headers
Security headers are essential HTTP response headers that strengthen your WordPress site’s defenses by mitigating various web-based attacks and reducing exposure to potential vulnerabilities.
This header prevents the browser from MIME type sniffing, which occurs when browsers try to detect the file type from content.
This header protects your site from clickjacking attacks by controlling whether your website can be displayed within an iframe on another site.
his header restricts which features and APIs the browser is allowed to use when displaying your site.
Enforces the use of HTTPS by telling the browser to only communicate with your site over secure, encrypted connections.
Controls how much referrer information is sent along with requests when users navigate between different sites.
Defines which content sources (such as scripts, stylesheets, or images) are considered safe to load.
Disable Vulnerable Settings
Disabling specific WordPress features is a crucial step in fortifying your website against potential security risks.
Disabling XML-RPC reduces the risk of unauthorized login attempts.
Disabling WordPress User Enumeration enhances security by preventing attackers from discovering usernames.
Disabling this option prevents hackers from injecting malicious code if they gain access to your admin area.
Disabling this feature prevents unauthorized users from accessing your site’s data.
Turning off commenting reduces the chances of spam or malicious links being posted, as well as injection attacks.
Disabling this feature hides your site’s version, making it harder for attackers to exploit any outdated components.

Detailed Security Reports
The PDF security report generated by our Guard Dog Security plugin will provide a comprehensive overview of the site’s current security status, offering valuable insights into both secured aspects and areas requiring further attention.
Your Brand Not Ours
The white label settings allow users to customize various aspects of the Guard Dog Security plugin, creating a unique and branded experience tailored to your organization. These options ensure that the plugin fits seamlessly within your site’s overall branding and workflow.
Secure Your Site Today/ Supreme Security
All day every day your site is {secure}
SAFE & EASY
Guard Dog Security Service
This service provides a complete security solution to ensure your WordPress website is fully protected from threats and vulnerabilities. It safeguards critical files from unauthorized changes, blocks common hacker entry points, and restricts unauthorized access by securing your login page and user registration processes. We will also react to any infections your site might receive at no additional cost.


